一、安装部署dashboard
1.部署(按官方文档)
在git上找到dashboard项目,可直接点击这里,执行如下命令。若网路问题无法执行成功,可以先下载配置文件recommended.yaml,然后基于此yaml配置文件创建相关资源。(若需此文件可联系作者获取)
[root@master1 ~]# kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0/aio/deploy/recommended.yaml
2.更改service类型
查看默认service信息
[root@master1 deploy-yaml]# kubectl describe svc kubernetes-dashboard -n kubernetes-dashboard Name: kubernetes-dashboard Namespace: kubernetes-dashboard Labels: k8s-app=kubernetes-dashboard Annotations: Selector: k8s-app=kubernetes-dashboard Type: ClusterIP IP: 10.99.178.83 Port: <unset> 443/TCP TargetPort: 8443/TCP Endpoints: 10.244.0.3:8443 Session Affinity: None Events: <none>
通过打补丁等方式修改service类型从ClusterIP改为NodeIP
[root@master1 ~]# kubectl patch svc kubernetes-dashboard -n kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}'
service/kubernetes-dashboard patched
查看更改后service的nodeport
[root@master1 ~]# kubectl get svc -n kubernetes-dashboard NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE dashboard-metrics-scraper ClusterIP 10.98.49.20 <none> 8000/TCP 15m kubernetes-dashboard NodePort 10.99.178.83 <none> 443:31049/TCP 15m
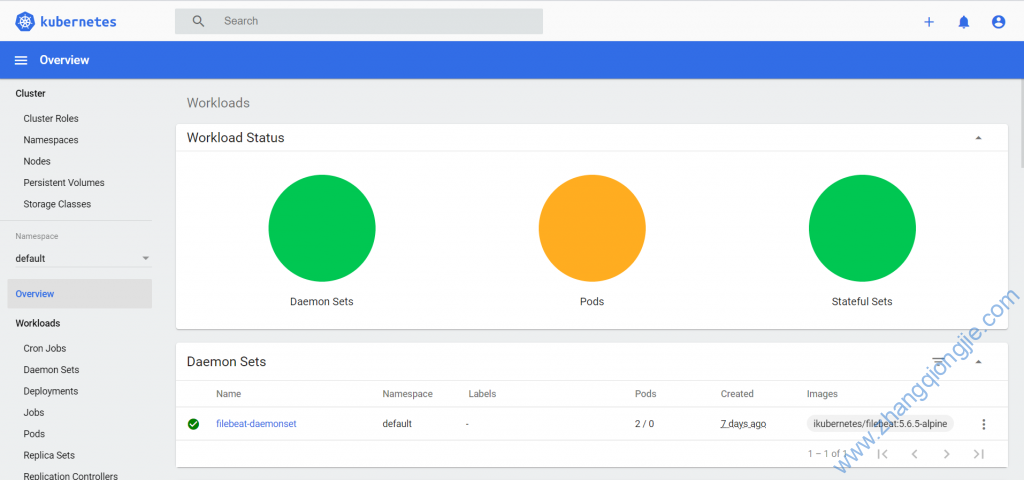
3.打开dashboard网页
如下图:
二、配置登录dashboard认证信息
登录kubernetes dashboard有token和kubeconfig配置两种认证登录方式,认证账户必须是serviceaccount,下面将两种认证方式分别进行操作演示。
方式一:token认证
一、多权限token认证
1.创建ServiceAccount账号
[root@master1 pki]# kubectl create serviceaccount dashboard-admin -n kubernetes-dashboard serviceaccount/dashboard-admin created [root@master1 pki]# kubectl get sa -n kubernetes-dashboard NAME SECRETS AGE dashboard-admin 1 18s default 1 59m kubernetes-dashboard 1 59m
2.clusterrolebinding绑定sa
使用clusterrolebinding绑定sa账号dashboard-admin
[root@master1 pki]# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:dashboard-admin clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created
3.查看token
将获取到的token直接复制到kubernetes dashboard登录复选框即可进行登录。
[root@master1 pki]# kubectl get secret -n kubernetes-dashboard
NAME TYPE DATA AGE
dashboard-admin-token-s4d8w kubernetes.io/service-account-token 3 6m12s
dashboard-cert Opaque 2 12m
default-token-wjlcg kubernetes.io/service-account-token 3 65m
kubernetes-dashboard-certs Opaque 0 65m
kubernetes-dashboard-csrf Opaque 1 65m
kubernetes-dashboard-key-holder Opaque 2 65m
kubernetes-dashboard-token-dc62x kubernetes.io/service-account-token 3 65m
[root@master1 pki]# kubectl describe secret dashboard-admin-token-s4d8w -n kubernetes-dashboard
Name: dashboard-admin-token-s4d8w
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: 033e763f-fca9-4cf5-b334-552ffe47ebb5
Type: kubernetes.io/service-account-token
Data
====
token: eyJhbGciOiJSUzI1NiIsImtpZCI6InJhOXdtTVE1OE44czBIb3BCQTVYbXduc2g2UTJNbW5tdE5SN09CQWFxeTAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tczRkOHciLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMDMzZTc2M2YtZmNhOS00Y2Y1LWIzMzQtNTUyZmZlNDdlYmI1Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmVybmV0ZXMtZGFzaGJvYXJkOmRhc2hib2FyZC1hZG1pbiJ9.J0mneIAsob60TfgLSUXRMQNai95VN-COCIUvmYhq_Br0s847ruvLvXpk4EVhMV0BUZUNGNIVv4xJmxI0sTk5mNQJ1bQyU3Cmf7xbsroBlUWZB_cNrzJPw0mXDtKdjcnzKltIr7kF4ah_E7dCaxchD1eD5GRjl0yK4PDup7uvaGYQFvsTXlHFwd1M1K0jLgOx48NZaSDcgm5YlGH1k4lr0-zPLlNaAarj27VC95nuaEoC7XP26xnTtasUWLyNUzOjv31do08_muVeF8nplnQVhNjoO5yUJlSlo2nTYzS3RhtoDjqJtfUkxkIxw_P_mI76LwL-wth3jqzOBTGDrPP0PQ
ca.crt: 1025 bytes
namespace: 20 bytes
二、单权限token认证
设置sa只能访问default名称空间的信息,方法如下:
您暂时无权查看此隐藏内容!
7.通过配置文件登录
获取配置文件,即可通过此配置文件进行登录。
内容查看价格5.99元立即支付
注意:本站少数资源收集于网络,如涉及版权等问题请及时与站长联系,我们会在第一时间内与您协商解决。如非特殊说明,本站所有资源解压密码均为:zhangqiongjie.com。
作者:1923002089
 琼杰笔记
琼杰笔记





评论前必须登录!
注册